
Table of Contents

Network Address Translation (NAT)
NAT Overview
Why Use NAT?
NAT Operation
Configuring NAT
Verifying NAT
Troubleshooting NAT
Implementation Considerations
Summary
Review Questions

-
NAT Overview
-
Why Use NAT?
-
NAT Operation
-
Configuring NAT
-
Verifying NAT
-
Troubleshooting NAT
-
Implementation Considerations
-
Summary
-
Review Questions
NAT Overview
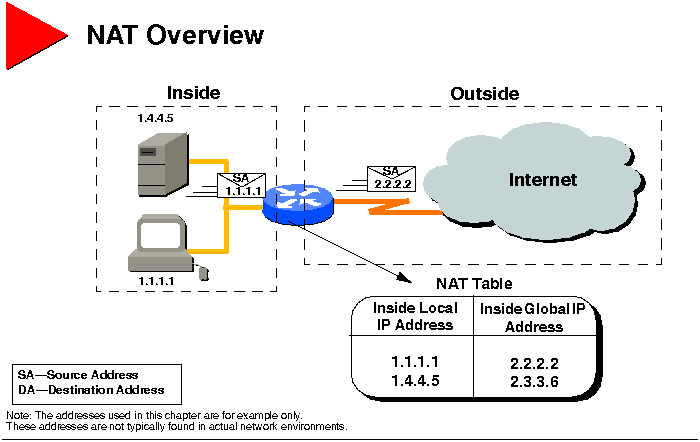
IP address depletion is a key problem facing the Internet. To assist
in maximizing the use of your registered IP addresses, Cisco IOS Release
11.2 software implements Network Address Translation (NAT). This feature,
which is Cisco's implementation of RFC 1631, The IP Network Address
Translator, is a solution that provides a way to use the same IP addresses
in multiple internal stub networks, thereby reducing the need for registered
IP addresses. Supported NAT features include:
-
Static address translation---Establishes a one-to-one mapping between inside
local and global addresses.
-
Dynamic source address translation---Establishes a dynamic mapping between
the inside local and global addresses. This is done by describing the local
addresses to be translated and the pool of addresses from which to allocate
global addresses, and associating the two. The router will create translations
as needed.
-
Address overloading---You can conserve addresses in the inside global address
pool by allowing source ports in TCP connections or UDP conversations to
be translated. When different inside local addresses map to the same inside
global address, each inside host's TCP or UDP port numbers are used to
distinguish between them.
-
TCP load distribution---A dynamic form of destination translation can be
configured for some outside-to-inside traffic. Once a mapping is set up,
destination addresses matching an access list are replaced with an address
from a rotary pool. Allocation is done on a round-robin basis, and only
when a new connection is opened from the outside to the inside. All non-TCP
traffic will be passed untranslated (unless other translations are in effect).
NAT Terminology
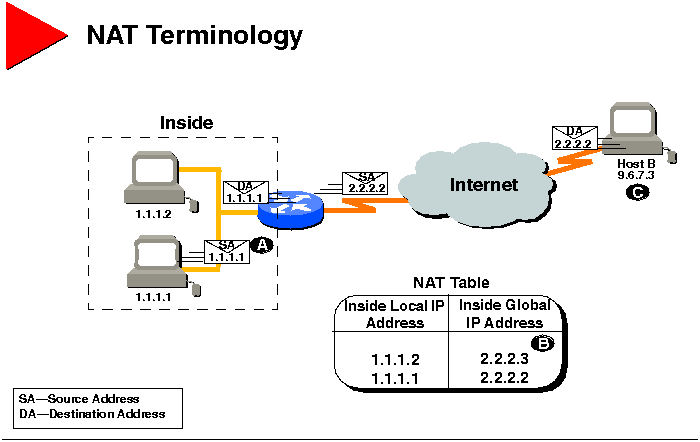
The following terms relate to NAT.
| Term |
Definition |
| Inside Local IP Address (A) |
The IP address assigned to a host on the inside network.
The address was globally unique but obsolete, allocated from RFC 1918,
Address Allocation for Private Internet Space, or randomly picked. |
| Inside Global IP Address (B) |
A legitimate IP address (assigned by the NIC or service
provider) that represents one or more inside local IP addresses to the
outside world. The address was allocated from globally unique address space,
typically provided by the ISP. |
| Outside Global IP Address (C) |
The IP address that was assigned to a host on the outside
network by its owner. The address was allocated from a globally routable
address space. |
| Outside Local IP Address |
The IP address of an outside host as it appears to the inside
network. The address was allocated from address space routable on the inside,
or possibly allocated from RFC 1918, for example. |
| Simple Translation Entry |
A translation entry that maps one IP address to another. |
| Extended Translation Entry |
A translation entry that maps one IP address and port pair
to another. |
Why Use NAT?
Use NAT in the following situations:
-
When you want to connect to the Internet but not all the hosts have globally
unique IP addresses. NAT technology enables private IP internetworks that
use nonregistered IP addresses to connect to the Internet. A NAT router
is placed on the border of a stub domain (referred to as the inside network)
and a public network such as the Internet (referred to as the outside network),
and translates the internal local addresses into globally unique IP addresses
before sending packets to the outside network.
-
NAT takes advantage of the fact that relatively few hosts in a stub domain
communicate outside of the domain at any given time. Because most of the
hosts do not communicate outside of their stub domain, only a subset of
the IP addresses in a stub domain must be translated into globally unique
IP addresses when outside communication is necessary.
-
When you need to modify your internal addresses because of changing ISPs.
For example, NAT can be used to translate the appropriate addresses. This
enables you to change addresses incrementally, without changes to hosts
or routers other than those bordering stub domains.
-
When you want to do basic load sharing. You can map outside IP addresses
to inside IP addresses using the TCP Load Distribution feature.
NAT Operation
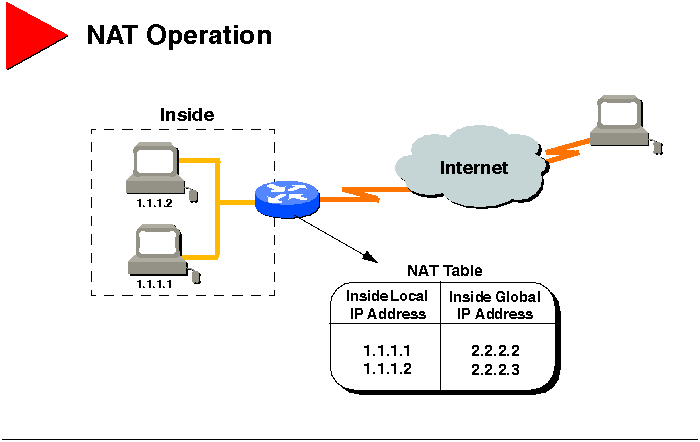
NAT can be used to perform several functions. This section discusses
the operation of the following NAT functions:
-
Translating Inside Local Addresses
-
Overloading Inside Global Addresses
-
Handling Overlapping Networks
-
TCP Load Distribution
Translating Inside Local Addresses
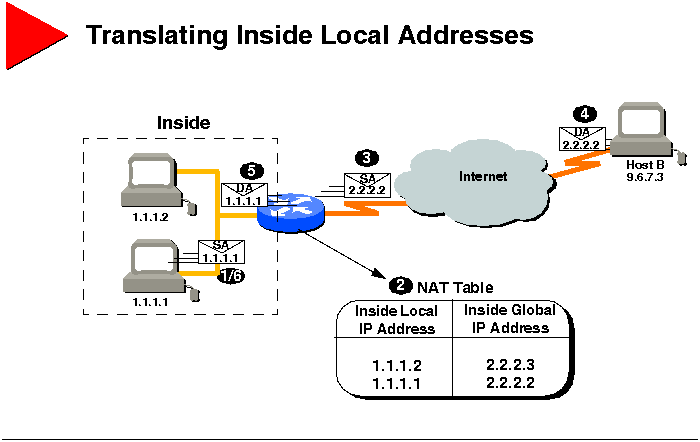
The graphic illustrates NAT operation when NAT is used to translate
addresses from inside your network to destinations outside of your network.
-
User at Host 1.1.1.1 opens a connection to Host B.
-
The first packet that the router receives from 1.1.1.1 causes the router
to check its NAT table.
If a translation is found because it has been statically configured,
the router continues to step 3.
If no translation is found, the router determines that address 1.1.1.1
must be translated. So the router allocates a new address and sets up a
translation of the inside local address 1.1.1.1 to a legal global address
from the dynamic address pool. This type of translation entry is referred
to as a simple entry.
-
The router replaces 1.1.1.1's inside local IP address with the selected
inside global address and forwards the packet.
-
Host B receives the packet and responds to 1.1.1.1 using the inside global
IP address 2.2.2.2.
-
When the router receives the packet with the inside global IP address,
the router performs a NAT table lookup using the inside global address
as the reference. The router then translates the address to 1.1.1.1's inside
local address and forwards the packet to 1.1.1.1.
-
1.1.1.1 receives the packet and continues the conversation. For each packet,
the router performs steps 2 through 5.
Overloading Inside Global Addresses
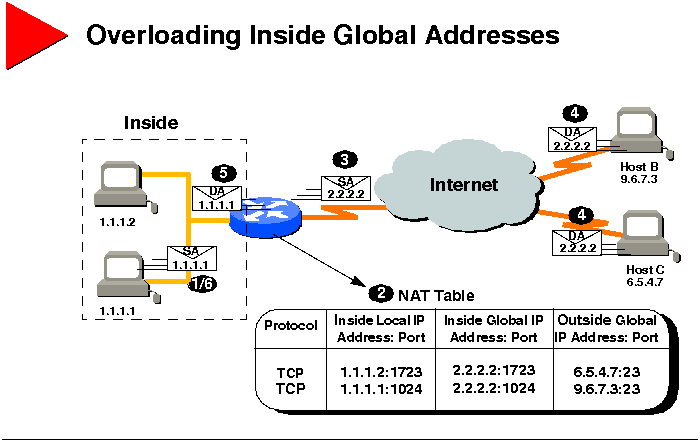
The graphic illustrates NAT operation when a single inside global address
can be used to represent multiple inside local addresses simultaneously.
-
User at Host 1.1.1.1 opens a connection to Host B.
-
The first packet the router receives from 1.1.1.1 causes the router to
check its NAT table.
If no translation is found, the router determines that address 1.1.1.1
must be translated. The router allocates a new address and sets up a translation
of the inside local address 1.1.1.1 to a legal global address. If overloading
is enabled, and another translation is active, the router will reuse the
global address from that translation and save enough information to be
able to distinguish it from the other translation entry. This type of entry
is called an extended entry.
-
The router replaces 1.1.1.1's inside local IP address with the selected
inside global address and forwards the packet.
-
Host B receives the packet and responds to 1.1.1.1 using the inside global
IP address 2.2.2.2.
-
When the router receives the packet with the inside global IP address,
the router performs a NAT table lookup using the inside global address
and port number, and the outside address and port number as the references.
The router then translates the address to 1.1.1.1's inside local address
and forwards the packet to 1.1.1.1.
-
1.1.1.1 receives the packet and continues the conversation. For each packet,
the router performs steps 2 through 5.
Handling Overlapping Networks
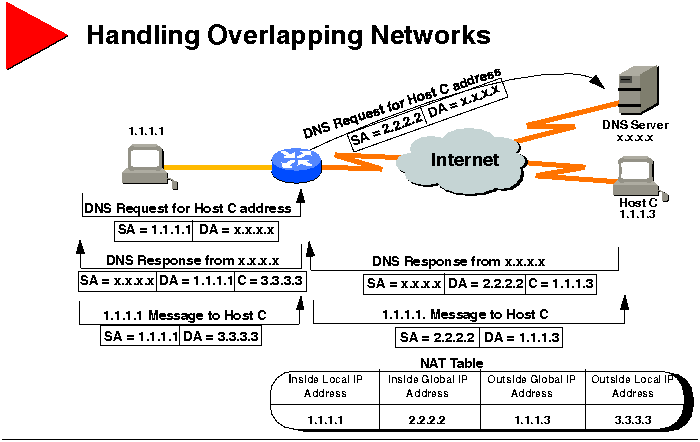
The graphic illustrates NAT operation when addresses in the inside network
overlap with addresses that are in the outside network.
-
User at 1.1.1.1 opens a connection to Host C (1.1.1.3) so 1.1.1.1 does
a name-to-address lookup to a DNS server.
-
The router intercepts the DNS reply and translates the returned address
if there is an overlap. In this case, 1.1.1.3 overlaps with an inside address.
To translate the return address of Host C, the router creates a simple
translation entry that maps the overlapping address 1.1.1.3 to an address
from a separately configured outside local address pool. In this example,
the address is 3.3.3.3.
-
The router then forwards the DNS reply to 1.1.1.1. The reply has Host C's
address as 3.3.3.3. At this point, 1.1.1.1 opens a connection to 3.3.3.3.
-
When the router receives the packet for Host C, the router sets up a translation
that maps the inside local and global addresses and outside global and
local addresses. The router does this by replacing the source address of
1.1.1.1 with the inside global address 2.2.2.2 and replacing the destination
address of 3.3.3.3 with Host C's outside global address 1.1.1.3.
-
Host C receives a packet and continues the conversation.
For each packet sent between 1.1.1.1 and Host C, the router does a
lookup, replaces the destination address with the inside local address,
and replaces the source address with the outside local address.
TCP Load Distribution
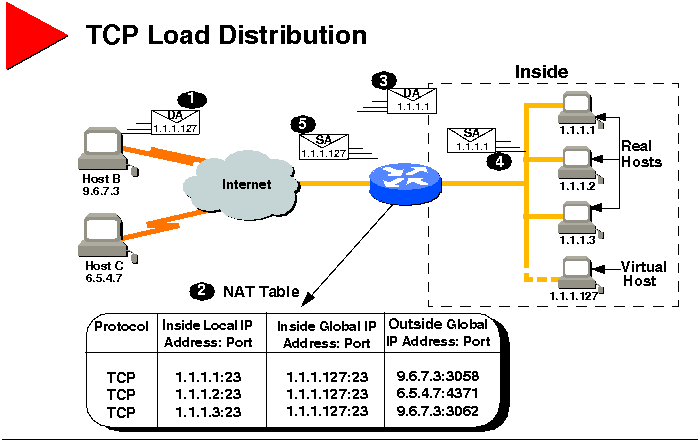
The graphic illustrates NAT operation when NAT is used to map one virtual
host to several real hosts.
-
User on Host B (9.6.7.3) opens a TCP connection to the virtual host at
1.1.1.127.
-
The router receives the connection request and creates a new translation
allocating the next real host (1.1.1.1) for the inside local IP address.
-
The router replaces the destination address with the selected real host
address and forwards the packet.
-
Host 1.1.1.1 receives the packet and responds.
-
The router receives the packet and performs a NAT table lookup using the
inside local address and port number and outside address and port number
as the key. The router then translates the source address to the address
of the virtual host and forwards the packet.
The next connection request will cause the router to allocate 1.1.1.2 for
the inside local address.
Configuring NAT
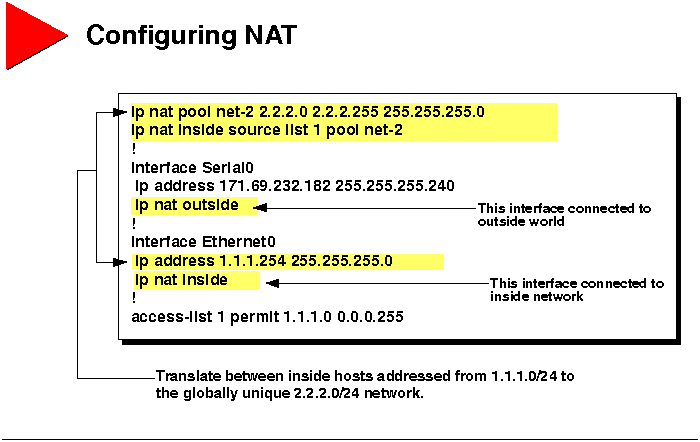
This section includes details about how to configure various NAT capabilities.
Configuring NAT for Basic Local IP Address Translation
The procedure used to enable basic local IP address translation is as
follows.
Step 1 At a minimum, IP routing and appropriate IP addresses
must be configured on the router.
Step 2 If you are doing static address translations
for inside local addresses, define the addresses.
-
-
router(config)#ip nat inside source static local-ip global
ip
Step 3 If you are doing dynamic translations, define a
standard IP access list for the inside network.
Step 4 If doing dynamic translation, define an IP NAT
pool for the inside network.
-
-
router(config)#ip nat pool name start-ip end-ip {netmask
netmask | prefix-length prefix-length}
-
Define a pool of contiguous addresses using start address, end address,
and netmask or prefix length. These addresses will be allocated as needed.
Step 5 If you are doing dynamic translation, define a map
between the access list and the IP NAT pool.
-
-
router(config)#ip nat inside source list access-list-number
pool name
Step 6 Enable NAT on at list one inside and one outside
interface.
-
-
router(config-if)#ip nat {inside | outside}
-
Only packets moving between "inside" and "outside" interfaces can be translated.
For example, if a packet is received on an "inside" interface but is not
destined for an "outside" interface, it will not be translated.
Configuring Inside Global Address Overloading
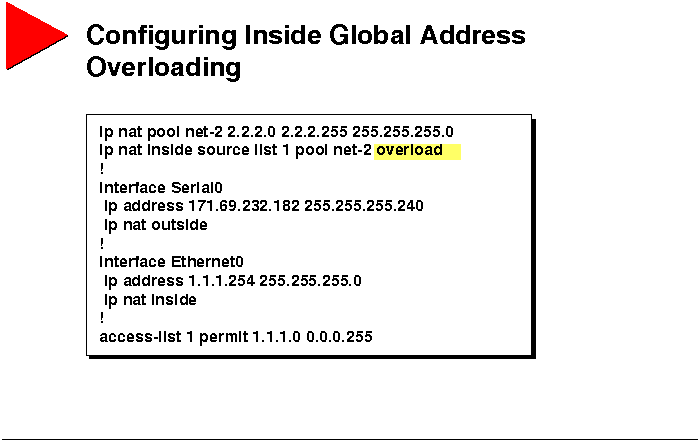
The procedure used to configure inside global address overloading is
as follows.
Step 1 At a minimum, IP routing and appropriate IP addresses
must be configured on the router.
Step 2 Configure dynamic address translation, as described
in the "Configuring NAT for Basic Local IP Address Translation" section.
-
-
When you define the mapping between the access list and the IP NAT pool
using the following command, add the overload keyword to the command:
-
router(config)#ip nat inside source list access-list-number
pool name overload
Step 3 Enable NAT on the appropriate interfaces.
-
-
router(config-if)#ip nat {inside | outside}
Configuring NAT to Translate Overlapping Addresses
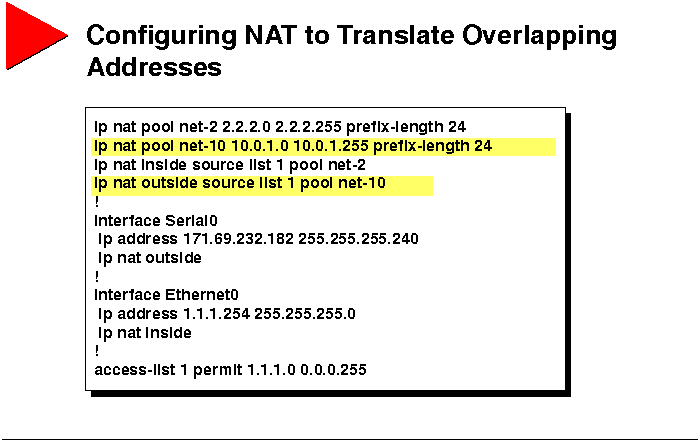
The procedure used to configure overlapping address translation is as
follows.
Step 1 At a minimum, IP routing and appropriate IP addresses
must be configured on the router.
Step 2 Define the standard IP access list for the inside
network, as previously discussed.
Step 3 Define an IP NAT pool for the inside network,
as previously discussed.
-
-
router(config)#ip nat pool name start-ip end-ip {netmask
netmask | prefix-length prefix-length}
Step 4 Define an IP NAT pool for the outside network.
-
-
router(config)#ip nat pool name start-ip end-ip {netmask
netmask | prefix-length prefix-length}
Step 5 Define mapping between the access list and the inside
global pool, as previously discussed.
-
-
router(config)#ip nat inside source list access-list-number
pool name [overload]
Step 6 Define mapping between the access list and the outside
local pool using the following command:
-
-
router(config)#ip nat outside source list access-list-number
pool name
Step 7 Enable NAT on the appropriate interface, as previously
discussed.
-
-
router(config-if)#ip nat {inside | outside}
Configuring TCP Load Distribution
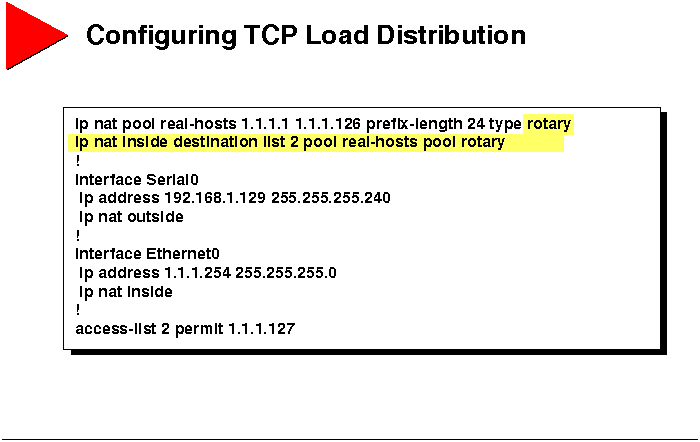
The procedure used to configure TCP load distribution is as follows.
Step 1 At a minimum, configure IP routing and appropriate
IP addresses on the router.
Step 2 Define a standard IP access list with a permit
statement for the virtual host.
Step 3 Define an IP NAT pool for the real hosts, making
sure it is a rotary type pool.
-
-
router(config)#ip nat pool name start-ip end-ip {netmask
netmask | prefix-length prefix-length} type
rotary
Step 4 Define a mapping between the access list and the
real host pool.
-
-
router(config)#ip nat inside destination list access-list-number
pool name
Step 5 Enable NAT on the appropriate interface, as previously
discussed.
-
-
router(config-if)#ip nat {inside | outside}
Verifying NAT
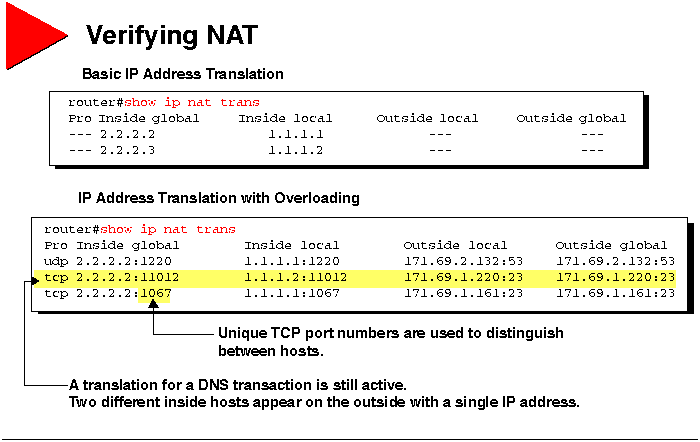
This section lists show and clear commands that are used
to verify NAT operation.
The following commands can be used to verify NAT operation.
| Command |
Description |
| show ip nat translations [verbose] |
Shows active translations. |
| show ip nat statistics |
Shows translation statistics. |
Clearing NAT Translation Entries
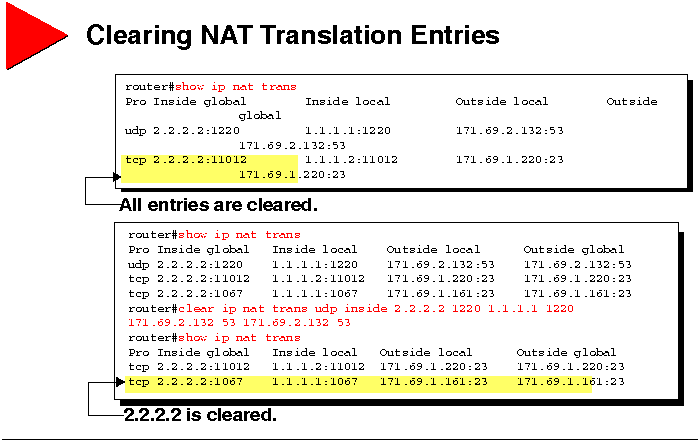
If you need to clear a dynamic translation entry, use the following
commands.
| Command |
Description |
| clear ip nat translation * |
Clears all translation entries. |
| clear ip nat translation inside global-ip local-ip
[outside local-ip global-ip] |
Clears a simple translation entry containing an inside translation,
or both an inside and outside translation. |
| clear ip nat translation outside local-ip global-ip |
Clears a simple translation entry containing an outside
translation. |
| clear ip nat translation protocol inside
global-ip global-port local-ip local-port [outside local-ip
local-port global-ip global-port] |
Clears an extended entry (in its various forms). |
Troubleshooting NAT
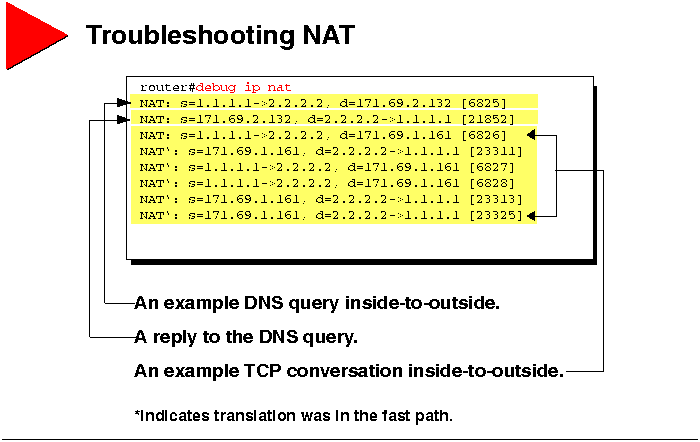
If you need to use a trace on NAT operation, use the following command.
| Command |
Description |
| debug ip nat [list | detailed] |
Displays a line of output for each packet that gets translated. |
As shown in the example, decode the debug output using the following keys.
-
The asterisk next to "NAT" indicates that the translation is occurring
in the fast path. The first packet in a conversation will always go through
the slow path (be process-switched). The remaining packets will go through
the fast path if a cache entry exists.
-
s=171.69.1.161 is the source address.
-
d=2.2.2.2 is the destination address.
-
2.2.2.2->1.1.1.1 indicates that the address was translated.
-
The value in brackets is the IP identification number. This information
may be useful for debugging because it enables you to correlate with other
packet traces from Sniffers, for example.
Implementation Considerations
Evaluate the following considerations before implementing this feature:
-
Translation introduces delays into the switching paths.
-
NAT makes some applications that use IP addresses difficult or impossible
to use. For example, public World Wide Web pages that have links expressed
using local IP addresses rather than DNS names will not be usable by outside
hosts.
-
NAT hides the "real" identity of hosts.
-
All packets that need to be translated must go through the NAT router,
which may place limitations on the network design.
Summary
This chapter discussed how NAT operates and when it can be used. It
also summarized how you configure, verify, and troubleshoot this feature.
Review Questions
Answer the following questions about NAT.
-
What is the difference between a simple translation entry and an extended
translation entry? And, how is each used?
-
Give one example of when NAT could be used.
-
Assume your company's networks are addressed using subnets of 10.1.1.0/24,
and that your service provider has given you the globally unique network
192.1.1.0/24 to be used for accessing the Internet. What commands would
you configure to instruct the router to translate from 10.1.1.0/24 to 192.1.1.0/24
when accessing the Internet?
-
When viewing the show ip nat translations command, how can you determine
when an inside global address is being used for overloading inside global
addresses?
Answers to Review Questions
The following are the answers to the review questions.
-
What is the difference between a simple translation entry and an extended
translation entry? And, how is each used?
-
A simple entry is used for translating inside local addresses. It is a
one-for-one match between an inside local address and an inside global
address.
-
-
A simple translation entry results when a router allocates a new address
and sets up a translation of an inside local address, such as 1.1.1.1,
to a legal global address from the dynamic address pool.
-
An extended translation entry is used when you want to overload inside
global addresses by letting a single inside global address represent multiple
inside local addresses simultaneously.
-
-
An extended translation entry results when a router reuses a global address
from an existing translation and save enough information about the translation,
such as the TCP port number, to be able to distinguish it from the existing
translation entry.
-
Give one example of when NAT could be used.
NAT can be used when you:
-
Want to connect to the Internet but not all the hosts have globally unique
IP addresses. NAT technology enables private IP internetworks that use
nonregistered IP addresses to connect to the Internet.
-
Need to modify your internal addresses. NAT enables you to change addresses
incrementally, without changes to hosts or routers other than those bordering
stub domains.
-
Want to do basic load sharing.
-
Assume your company's networks are addressed using subnets of 10.1.1.0/24,
and that your service provider has given you the globally unique network
192.1.1.0/24 to be used for accessing the Internet. What commands would
you configure to instruct the router to translate from 10.1.1.0/24 to 192.1.1.0/24
when accessing the Internet?
-
To instruct the router to translate 10.1.1.1 through 10.1.1.254, do the
following: access-list 1 permit 10.1.1.1 0.0.0.254
-
To define the address pool, do the following: ip nat pool test 192.1.1.1
192.1.1.254 netmask 255.255.255.0 (Instead of the mask, you can write the
prefix; in this case it is 24.)
-
To map 10.1.1.0 to the address pool, do the following: ip nat inside source
list 1 pool test
-
Enable the translation on the inside interface using the command: ip nat
inside
-
Enable the translation on the outside interface using the command: ip nat
outside
-
When viewing the show ip nat translations command, how can you determine
when an inside global address is being used for overloading inside global
addresses?
An inside global address is listed for each inside local address it
represents. If it is representing three inside local addresses, it will
appear three times, each time with a different port number.
The port number of each entry will match the port number for the inside
local address it is representing. The port numbers are used to distinguish
between each inside local address that the single inside global address
is being used for.
Copyright Cisco Systems, Inc. -- Version 2.0 1/97



















