Table of Contents

Module 2 - Design the Network Structure
Section 1 - Design the Topology
Part C - Secure Models
Introduction
In this segment we will talk about secure topology models. Other aspects
of security such as encryption and access lists will be discussed in Section
6 of Module 2, "Provision Software Features." The information in this
class is not sufficient to learn all the nuances of internetwork security.
To learn more about internetwork security, read the book Firewalls and
Internet Security by Bill Cheswick and Steve Bellovin. It is published
by Addison Wesley. Also, by searching on the word "security" on Cisco's
Web site, you can keep up to date on security issues.
Secure topologies are often designed using a firewall. A firewall protects
one network from another untrusted network. This protection can be accomplished
in many different ways, but in principle, a firewall is a pair of mechanisms:
one blocks traffic, and the other permits traffic. Some firewalls place
a greater emphasis on blocking traffic, and others emphasize permitting
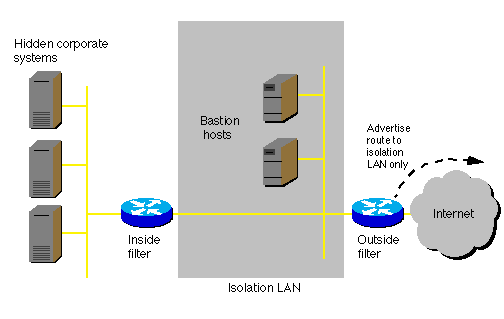
traffic. A simple firewall topology using routers is shown below.

You can design a firewall system using packet-filtering routers and
bastion hosts. A bastion host is a secure host that supports a limited
number of applications for use by outsiders. It holds data that outsiders
access, for example, Web pages, but is strongly protected from outsiders
using it for anything other than its limited purposes.
Three-Part Firewall System
The classic firewall system, called the "three-part firewall system," has
three specialized layers:
-
An isolation LAN that is a buffer between the corporate internetwork and
the outside world. (The isolation LAN is called the demilitarized zone
in some literature.)
-
A router that acts as an inside packet filter between the corporate internetwork
and the isolation LAN.
-
Another router that acts as an outside packet filter between the isolation
LAN and the outside internetwork.
Services available to the outside world are located on bastion hosts in
the isolation LAN, for example:
-
Anonymous FTP server
-
Web server
-
Domain Name Service (DNS)
-
Telnet
-
Specialized security software such as TACACS
The isolation LAN has a unique network number that is different from the
corporate network number. Only the isolation LAN network is visible to
the outside world. On the outside filter you should advertise only the
route to the isolation LAN.
If internal users need to get access to Internet services, allow TCP
outbound traffic from the internal corporate internetwork. Allow TCP packets
back in only if the ACK or RST bits are set. The established keyword
is used to indicate packets with ACK or RST bits set. All other TCP should
be blocked because new inbound TCP sessions could result from hackers trying
to establish sessions with internal hosts. The following list summarizes
some rules for the three-part firewall system.
-
The inside packet filter router should allow inbound TCP packets from established
sessions.
-
The outside packet filter router should allow inbound TCP packets from
established TCP sessions.
-
The outside packet filter router should also allow packets to specific
TCP or UDP ports going to specific bastion hosts (including TCP SYN packets
that are used to establish a session.)
Block traffic from firewall routers and hosts. The firewall routers and
hosts themselves are likely to be a jumping-off point for hackers.
Keep bastion hosts and firewall routers simple. They should run as few
programs as possible. The programs should be simple because simple programs
have fewer bugs than complex programs. Bugs introduce possible security
holes.
Do not enable any unnecessary services or connections on the outside
filter router. A list of suggestions for implementing the outside filter
router follows:
-
Turn off Telnet access (no virtual terminals defined).
-
Use static routing only.
-
Do not make it a TFTP server.
-
Use password encryption.
-
Turn off proxy ARP service.
-
Turn off finger service.
-
Turn off IP redirects.
-
Turn off IP route caching.
-
Do not make it a MacIP server.
Cisco PIX Firewall
To provide stalwart security, hardware firewall devices can be used in
addition to or instead of packet-filtering routers. For example, in the
graphic of the three-part firewall system shown earlier, a hardware firewall
device could be installed on the isolation LAN. A hardware firewall device
offers the following benefits:
-
Less complex and more robust than packet filters
-
No downtime required for installation
-
No upgrading of hosts or routers is required
-
No day-to-day management is necessary
Cisco's PIX Firewall
is a hardware device that offers features listed above as well as full
outbound Internet access from unregistered internal hosts. IP addresses
can be assigned from the private ranges, as defined in RFC
1918. (We will talk more about private addresses in Section
4 of Module 2, "Design Network-Layer Addressing and Naming Model."
The PIX Firewall uses a protection scheme called Network Address Translation
(NAT) that allows internal users access to the Internet, while protecting
internal networks from unauthorized access.
The PIX Firewall provides firewall security without the administrative
overhead and risks associated with UNIX-based or router-based firewall
systems. The PIX Firewall operates on a secure real-time kernel, not on
UNIX. The network administrator is provided with complete auditing of all
transactions, including attempted break-ins.
The PIX Firewall supports data encryption with the Cisco PIX Private
Link, a card that provides secure communication between multiple PIX systems
over the Internet using the data encryption standard (DES).
The PIX Firewall provides TCP and UDP connectivity from internal networks
to the outside world using a scheme called "adaptive security." All inbound
traffic is verified for correctness against the following connection state
information:
-
Source and destination IP addresses
-
Source and destination port numbers
-
Protocols
-
TCP sequence numbers (which are randomized to eliminate the possibility
of hackers guessing numbers)
PIX Firewall Security Features Tested
SRI Consulting (SRIC) recently conducted a set
of tests to evaluate the security features of PIX. SRIC configured
the product as a firewall to separate one LAN from another and ran penetration
scripts designed to allow unauthorized access. On the basis of these tests,
SRIC concluded that a properly configured PIX Firewall can provide a reliable
and secure interface between a company's internal network(s) and the Internet.
PIX Firewall resisted all of SRIC's many attempts to directly attack its
network interfaces. In addition, PIX Firewall did not allow access to any
computer on the internal network, even under conditions of severe input
overload.
Click on the Back button in your browser or click
here to go back to Section 1 of Module 2, "Design the Topology."
Copyright Cisco Systems, Inc. -- Version 2.0 7/98