
Table of Contents

Module 2 - Design the Network Structure
Section 1 - Design the Topology
Jones, Jones, & Jones: Solution
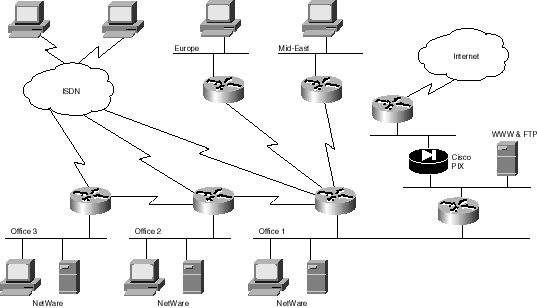
1. Draw a topology that will meet Mr. Jones's
requirements. Include only the high-level view of the location
of links and internetworking
devices. In a few sentences, describe how your topology meets the law
firm's needs.
-
Jones's need to improve competitiveness with technology is met with the
deployment of the Cisco routers. These products will provide the company
with the connectivity and functionality to operate on a global basis with
the ability to collaborate on its work as if it was a single office with
very affordable products that will not become obsolete. The private network
and firewall to the Internet will provide adequate security. The use of
the Ethernet switch in the larger offices will provide significant performance
advantages. The use of ISDN and asynch dial-in through the main Cisco router
provides a very economical, high-performance, and ubiquitous dial-in solution.
-
For foolproof network security, a three-part firewall system locates Jones's
Web/FTP server behind the first tier. To access this tier, users come through
a router that provides initial security. Beyond this first tier is Cisco's
PIX Firewall series, which represents the second-tier security perimeter.
In case there is a breach of security on the exposed segment, the PIX Firewall
series acts as a strong security barrier to prevent outside users from
gaining access to Jones’s private network. Coupling Cisco's PIX Firewall
series with Cisco routers running Cisco IOS software will provide Jones
with a powerful security solution that will allow it to sell its research
papers without fear of exposure of internal documents and files. It forces
hackers to penetrate multiple lines of defense.
2. The managing partner called. She wanted to
emphasize that unauthorized workstations should not be
allowed access to the
Internet. How have you accommodated this request in your design?
-
Static IP addresses should be assigned to specific users at the DHCP server.
All other addresses will then be filtered by the Internet router.
Click on the Back button in your browser to review Section 1 of Module
2. If you are finished with that section, click
here to go on to Section 2.
Copyright Cisco Systems, Inc. -- Version 2.0 7/98


